Painstaking Lessons Of Info About How To Detect Conficker With Nmap

When conficker.c or higher infects a system,.
How to detect conficker with nmap. Description = [[ checks if a host is infected with conficker.c or higher, based on conficker's peer to peer communication. The ports are random, but are seeded with the current week and the ip of. When conficker.c or higher infects a system, it opens four ports:
Nmap is short for network mapper. You will need to disable firewalls. Checks if a host is infected with conficker.c or higher, based on conficker's peer to peer communication.
You need the very latest version to get the scripts that will check for conficker. Intrusive, exploit, dos, vuln download: Detects microsoft windows systems infected by the conficker worm.
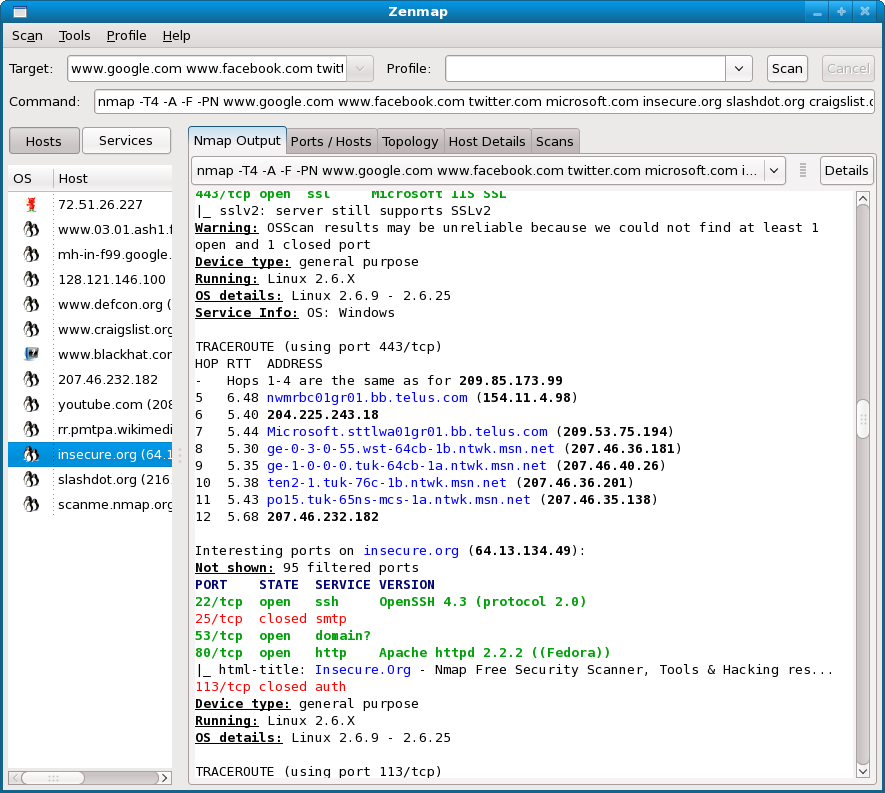
If you want to conduct a vulnerability scan, you can use nmap, which is a popular tool for the security testing process. This check is dangerous and it may crash systems. Now that you have the latest nmap compiled and installed you can scan your network(s) for the conficker worm.
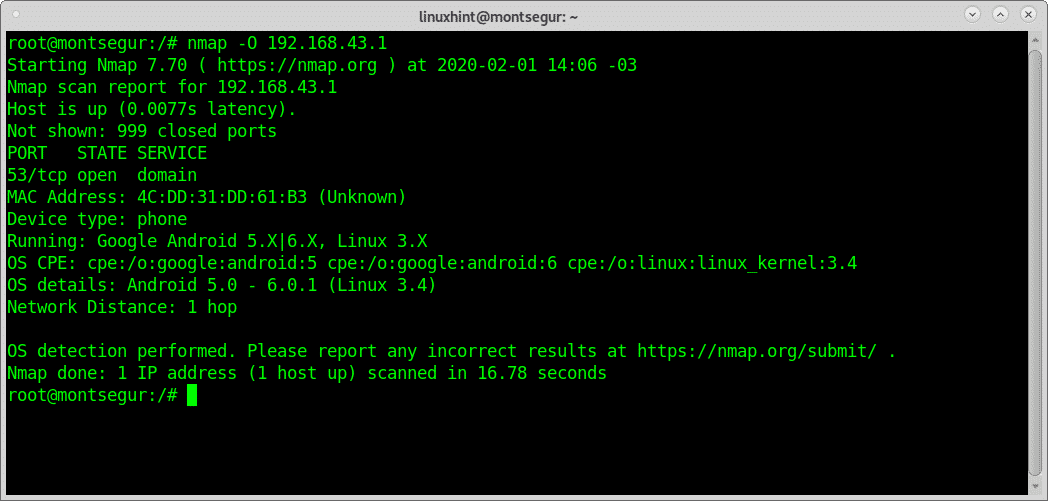
To scan for conficker, use a command such as: The version i used here was 4.85beta8. Now that we have the importance and common usage of smb, let us.
Hot on the coattails of the simple conficker scanner, i’ve added detection for conficker to nmap. You can scan your network for conficker with a command like: Let’s look at how to set up this tool as well as how to run a basic cve scan.
Scan for web servers and grep to show which ips are running web servers: Nmap is a powerful and versatile network. When conficker.c or higher infects a.
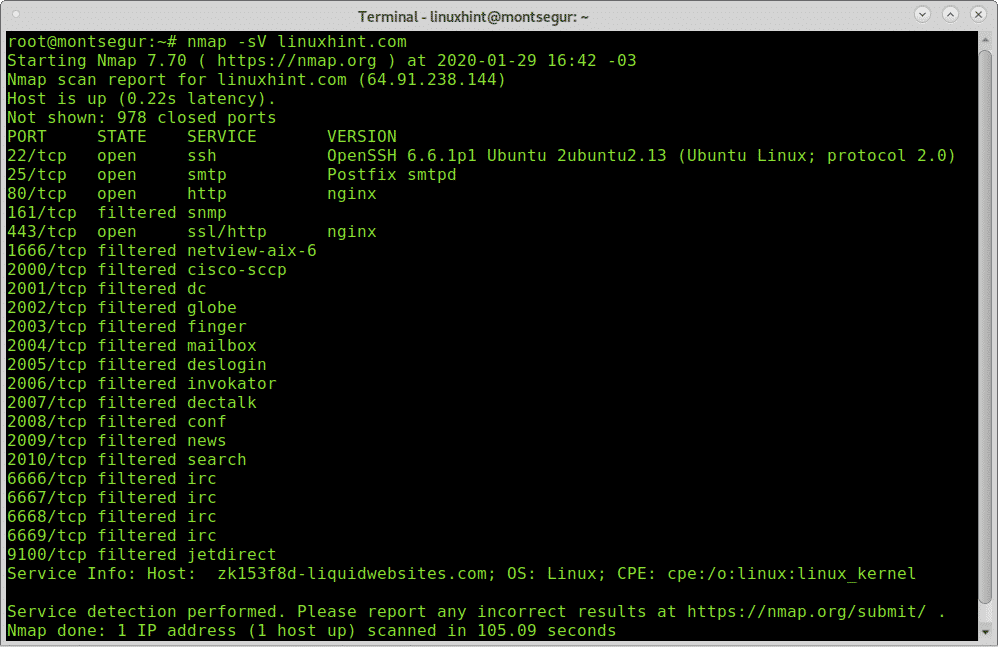
It helps identify hosts, services, and vulnerabilities, and is commonly used for. The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139.